
Shivank Gautam
Senior Backend Engineer, Educator
How One goto Broke the Internet
In 2014, Apple had a major security bug in their SSL implementation because of one extra line:
if ((err = SSLHashSHA1.update(&hashCtx, &signedParams)) != 0)
goto fail;
goto fail; // <- This line always runs!
if ((err = SSLHashSHA1.final(&hashCtx, &hashOut)) != 0)
goto fail;
That second goto fail; was not inside an if condition. So it always ran and skipped the final certificate check — basically saying any site was valid, even fake ones.
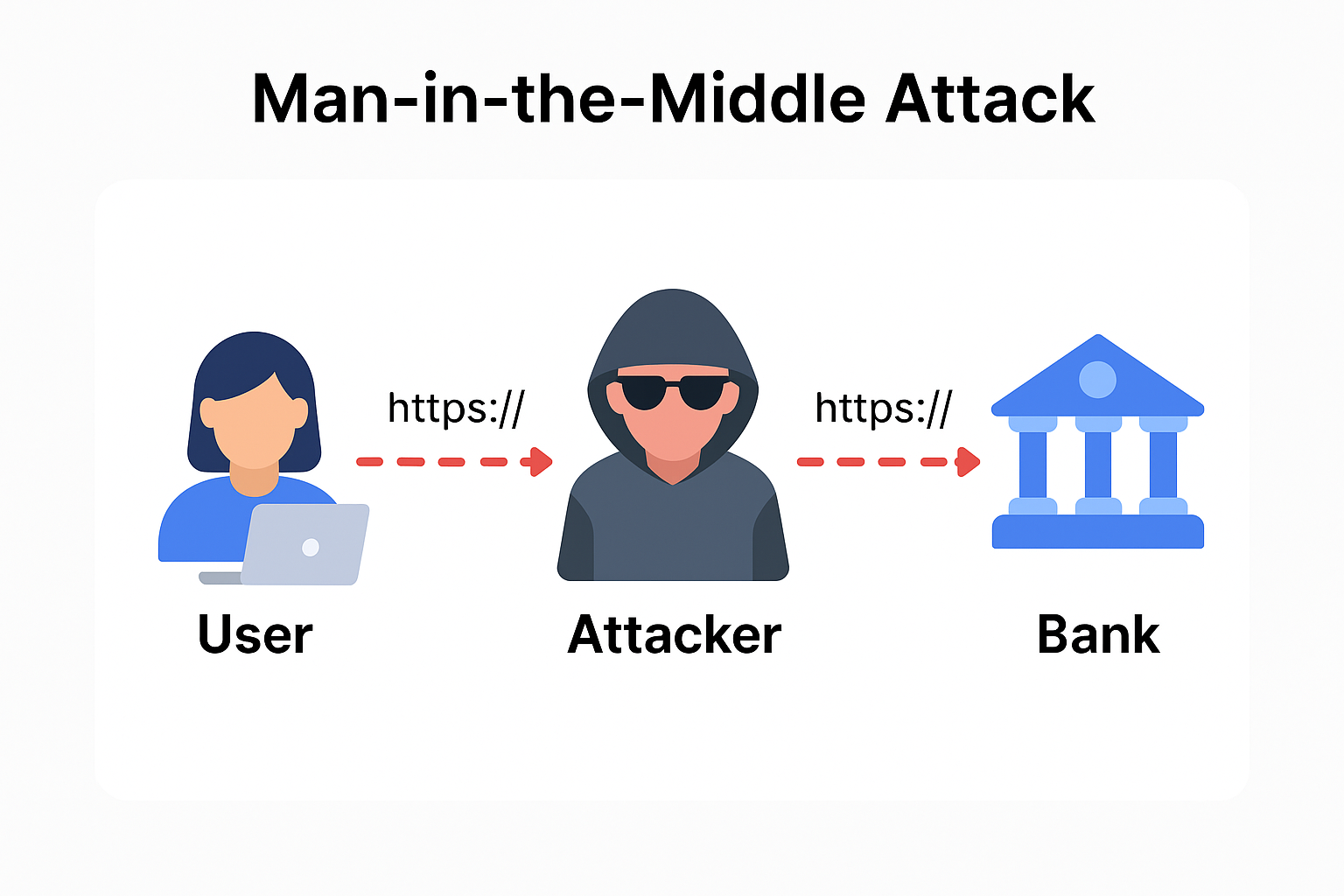
How could someone exploit this?
Imagine you're on café Wi-Fi. An attacker creates a fake hotspot and pretends to be yourbank.com. Your phone thinks it's secure, but it’s not. That’s a man-in-the-middle attack — and this bug made it easy.
Could this have been prevented?
Yes. A simple test like:
assert validate_ssl(fake_cert) == False
would likely have caught it. But there was no test — and millions were left exposed.
⚠️ Even one line of code can break trust. Write tests. Always.